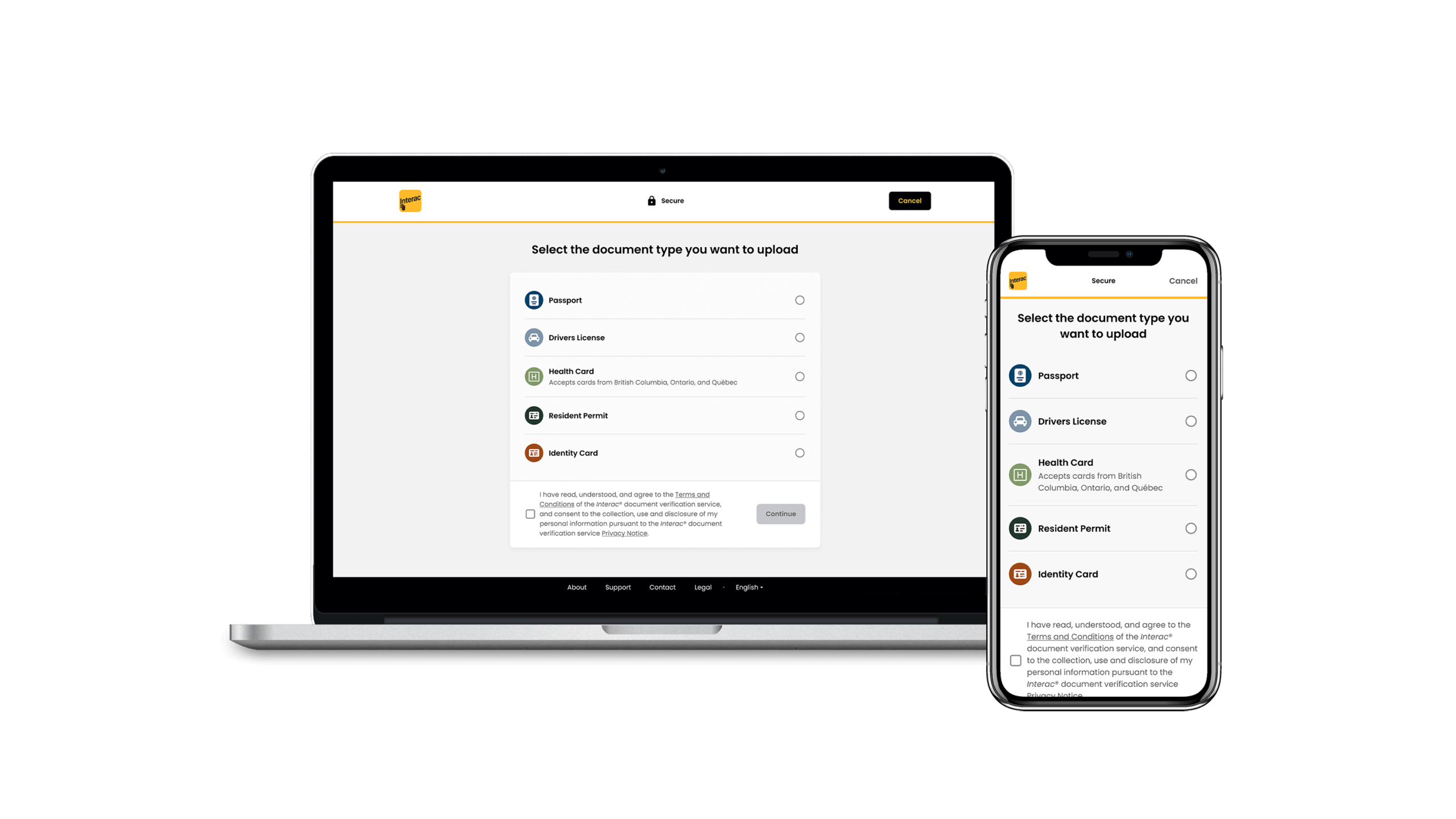
Interac® document verification service lets customers verify themselves using their phone and government-issued photo ID.
See HowUnlock new digital opportunities.
Your customers expect seamless and secure digital transactions, whenever and wherever they want. Meeting that challenge starts with confidently knowing they are who they say they are.
How can Interac Verified™ empower your business?
User-friendly. Business-friendly.
Interac Verified enables businesses to digitally verify customers’ data so they can conveniently and securely access services through future-ready verification solutions.

Document verification

Bank verification
With Interac® verification service, your customers can use their existing login credentials with a participating financial institution to quickly and securely verify their identity when creating an account, validated by a trusted party to help streamline the customer onboarding process.
Learn MoreExplore verification opportunities in a variety of Canadian industries.
Commerce
Verifying buyers and sellers for seamless online marketplace transactions.
Mobility
Validating data for carsharing, rentals, and more.
Healthcare
Facilitating online access to confidential health and medical records.
Transportation
Verifying data for passengers and commuters.
Real Estate
Helping to improve efficiency, convenience, and security by reducing identity or financial information fraud for renters, landlords, real estate sellers or buyers, and new mortgage applicants.
Immigration
Streamlining access to services and opportunities for new Canadians as applied to visas, permanent resident cards and citizenship documentation.
Government Services
Enabling access to tax information and government services.
Lottery & Gaming
Improving convenience and reducing fraud for Canadian gaming customers.
Air Travel
Improving security, efficiency, and convenience while reducing risk and fraud.
Employment
Validating candidate credentials and accreditations for employers.
Banking
Opening new financial services accounts (e.g., bank account, credit card, loan).
Integrating Interac verification hub
Businesses can deploy Interac Verified solutions using a single API. A complementary developer portal lets technology teams validate technical requirements and use cases to help them get up and running quickly.
Tune in to our Everyday Trust series.
In each episode, Debbie Gamble, Chief Innovation and New Ventures Officer at Interac, is joined by an expert to discuss the importance of trust within their industry and how credible, secure solutions can help fuel prosperity in Canada.
Watch NowDesigned for the future.
As the digital landscape evolves, so does the Interac Verified suite. It’s designed to support multiple technology standards so your business can confidently meet customers’ expectations now and in the future.
Partner with a brand Canadians trust.
Leveraging decades of experience in delivering secure payments, Interac Verified is making access to online transactions fast, easy, and secure for Canadians.
*As of 2022
**Per the 2022 Gustavson Trust Index based on 9,189 Canadian adult (aged 18+) consumers surveyed: https://www.uvic.ca/gustavson/brandtrust/assets/docs/final–gbti-2022-main-report.pdf